Review of Penetration Testing A Hands-On Introduction to Hacking
Wednesday, July 30, 2014
Helping train a computer security incident response team (CSIRT) comes with the territory when building out an enterprise incident response process. As I was reading No Starch's recently released Penetration Testing A Hands-On Introduction to Hacking book by Georgia Weldman I saw an opportunity. The book target's audience are beginners. In the author's words "I thought an introduction to pentesting would make the biggest impact on the audience I most wanted to reach." The opportunity I saw was the book can also be leveraged by people new to incident response. Specifically, new to responding to systems hit with either client-side or web application attacks. To see how a beginner pen testing book can become a beginner incident response book read on.
No Starch Press has a series of books with the word "practical" in their title. These books are the equivalent of an entire training for the cost of a book. The reason is because they take a practical approach. They provide supplemental material which allows the reader to do the same hands-on activities they are reading about throughout the book. Not only does the reader learn through reading but they learn by doing using the same tools and data described in the books. The Penetration Testing book may not have "practical" in its title but it follows the same approach, which is why it is a great book for beginners.
The book starts out by having the reader configure four different virtual machines (VMs). One VM is a Kali box, which is the platform the reader launches attacks from. The three other VMs (Windows XP, Windows 7, and Ubuntu) are configured very vulnerable to make it easier to attack them. As the reader progresses through the book they read about performing various attacks followed by actually doing the attacks against the vulnerable VMs. It's an excellent approach to expose beginners to pen testing. On the flip side, it's also an excellent approach to expose beginners to incident response. Not only does the reader get familiar with different attacks, vulnerabilities, and the payloads but they are creating compromised vulnerable VMs to examine after the fact. So the reader can compromise a system then examine the system to see what attack artifacts are present.
The book does cover numerous vulnerabilities and exploits. However, were two attack categories I thought excel at helping incident response beginners. Over the years, attacks targeting client-side and web applications have been a significant issue for organizations. These attacks are so common that sooner or later they will be encountered by most incident responders. As a result, exploring these attacks is of utmost important for people new to the IR field and the book addresses these attacks thought-out different chapters. The reader may gain a thing or two from the other attacks (i.e. MS08-067 exploitation) but the exploits used in those attacks are something they may not see outside of training environments due to their age.
One step to perform in addition to what is outlined in the Setting Up Your Virtual Lab chapter is to enable logging for Filezilla (FTP service) on the XP VM. To do so, access FileZill'a admin panel then select Edit -> Settings to get to the configuration window. In the logging section check the Enable Logging selection.
Before diving into the client-side or web application attacks I need to take a moment to outline where the reader needs to look for attack artifacts. I won't go into detail about all of the artifacts and will only cover the pertinent ones to explore the attacks for the Windows VMs.
One of the vulnerable applications installed on Windows XP is XAMPP. XAMPP is an "Apache distribution containing MySQL, PHP and Perl; this provides the VM with vulnerable web services. The following are the logs and artifacts of interest the reader would want to review after the attacks:
Apache logs location: C:\xampp\apache\logs
FileZilla log location: C:\xampp\FileZillaFTP\Logs
The Windows XP operating system artifacts of interest are:
NTFS Master File Table ($MFT)
NTFS Logfile ($Logfile)
Internet explorer browser artifacts
One of the applications installed on the Windows 7 VM is the web service IIS. The book provides a vulnerable web application (called BookApp) that runs on top of IIS. The ISS logging settings can be left in their default configuration. The following are the logs and artifacts of interest the reader would want to review after the attacks:
IIS logs location: C:\inetpub\logs\LogFiles\W3SVC1
Windows HTTP.sys error logging location: C:\Windows\System32\LogFiles\HTTPERR
The Windows 7 operating system artifacts of interest are:
NTFS Master File Table ($MFT)
NTFS Logfile ($Logfile)
NTFS Change Journal ($USNJrnl)
The last tidbit I'll cover before diving into the attacks is the need to stay organized. As I worked my way through the book I took notes to record when and what attack I performed against what vulnerable VM. This reference made things easier as I was examining the artifacts; it was easier to match up attacks against activity in the artifacts. The screenshot below shows a portion of the notes I kept
Keeping notes is not a necessity but something I highly recommend for beginners.
Artifacts left by client-side attacks have been well documented on this blog. To name a few: Java was documented here and here, Silverlight discussed here and here while Adobe Reader was mentioned here. Even though some artifacts have already been documented replicating client-side attacks is more beneficial than only reading research done by others. Actually performing the attack against a vulnerable VM shows a completely different perspective and one that can't be attained by just reading about artifacts. The image below shows the Windows XP parsed MFT around the time the system was compromised with the Aurora Internet Explorer exploit (the exploit is the htm page.)
The book covers numerous attacks against web applications on the Windows XP, Windows 7, and Ubuntu VMs. The variety of the attacks I thought provided a good starting point for exploring the different ways web servers and applications are compromised. In this post I'm only discussing a few items to demonstrate the traces left in certain artifacts showing these attacks took place.
Chapter 6 walks through a process for finding vulnerabilities on a VM. The chapter has the reader use the following methods: Nessus (vulnerability scanner), Nmap scripting engine (port scanner), Metasploit (exploitation framework), Nikto (web application scanner), and one manual technique. Exploring this aspect for incident response is important since for a system to be compromised a vulnerability had to be exploited. Seeing the traces left by the different methods provides an idea about what one may come across during examinations.
The image below shows the Nessus vulnerability scan activity in the Windows 7 IIS logs. The image is only a small portion of the logs but it illustrates how noisy vulnerability scanners are. This is obvious activity that most monitoring tools will detect fairly quickly. It's also activity that will most likely be tied to people authorized to perform this work for an organization and not an attacker.
In addition to the IIS logs in the W3SVC1 folder, the HTTP.sys error logging provides additional clues about the vulnerability scanning activity as shown below.
The Nmap script scan activity leaves traces in the logs as well but nothing close to the amount left by a vulnerability scanner. The image below shows the Windows 7 IIS logs where the Nmap script scan activity was located (note: the activity will be dependent on the script ran and won't always appear as it does in the image.)
Part III in the book has eight different chapters focused on different types of attacks. I won't rehash what all of the attacks are since the book's table of contents is adequate enough. One of the attacks was against a command execution vulnerability, which allows a person to execute commands against the system through the web application. In order to see the command's output - since the web application doesn't display - it requires the attacker (aka reader) to redirect it to a file on the server and then the file is accessed.
The image below shows the command being executed though the "subscribe to a newsletter" functionality (line in the middle.) It's not too apparent what is taking place since the HTTP method used is a POST to send data to the server. The data is not reflected in the URL. However, shortly after the POST there is a GET request for a file on the server named test.txt and the 200 status code means OK (file is there). The POST method may not be too revealing but the GET method reveals a file is on the server.
The server's MFT (parsed into a timeline) provides more clarity about the attack as shown below. The ipconfig.exe program executed at the same time as a new user (georgia) subscribed to a newsletter. Looking at the contents of test.txt shows it contains the ipconfig command output.
Another attack that was discussed is leveraging the PHPAdmin panel to execute SQL commands directly against a backend database. The attack involved executing a SQL command that creates a simple web shell on the system; shell only lets you execute commands in a supplied URL.
The Apache logs reveal the attack as seen in the image below. The line for the GET request at 21:17:01 (EDT) shows the URL containing the exact SQL command that creates the file called shell.php. The other highlighted lines show a request for the shell.php file followed by the various commands that were executed through the shell.
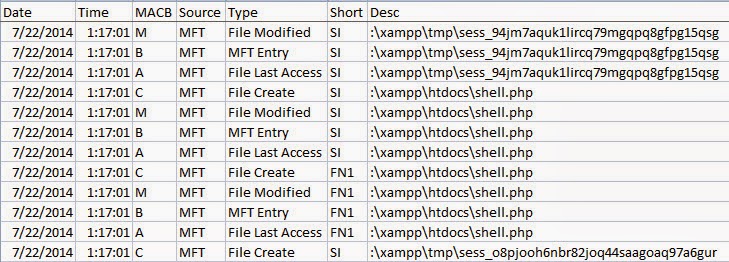
The server's MFT parsed into a timeline provides more clarity about the attack as shown below (time is in UTC).
As described in the book's introduction it is for beginners. Those who are new to pen testing field. I also see value in the book for incident response. For those who are either new to incident response without a background in offensive security or those who haven't been exposed to compromised web servers and applications. One shouldn't expect to know everything about investigating systems impacted by client-side and web attacks after working their way through the book. Heck, the reader may never see these exact attacks (outside of pen testers) against production systems. However, the reader will have a better understanding about attack vectors. The means by which an attacker can gain access to a system in order to deliver a payload or malicious outcome. The reader will have an even better understanding about the attack vector artifacts left on those systems. For anyone fitting what I just described should definitely pick up this book, build the VMs, attack the VMs, and then discover what traces they can find. It won't be the last step in their journey but it will be a good first one.
Practical Approach
No Starch Press has a series of books with the word "practical" in their title. These books are the equivalent of an entire training for the cost of a book. The reason is because they take a practical approach. They provide supplemental material which allows the reader to do the same hands-on activities they are reading about throughout the book. Not only does the reader learn through reading but they learn by doing using the same tools and data described in the books. The Penetration Testing book may not have "practical" in its title but it follows the same approach, which is why it is a great book for beginners.
The book starts out by having the reader configure four different virtual machines (VMs). One VM is a Kali box, which is the platform the reader launches attacks from. The three other VMs (Windows XP, Windows 7, and Ubuntu) are configured very vulnerable to make it easier to attack them. As the reader progresses through the book they read about performing various attacks followed by actually doing the attacks against the vulnerable VMs. It's an excellent approach to expose beginners to pen testing. On the flip side, it's also an excellent approach to expose beginners to incident response. Not only does the reader get familiar with different attacks, vulnerabilities, and the payloads but they are creating compromised vulnerable VMs to examine after the fact. So the reader can compromise a system then examine the system to see what attack artifacts are present.
The book does cover numerous vulnerabilities and exploits. However, were two attack categories I thought excel at helping incident response beginners. Over the years, attacks targeting client-side and web applications have been a significant issue for organizations. These attacks are so common that sooner or later they will be encountered by most incident responders. As a result, exploring these attacks is of utmost important for people new to the IR field and the book addresses these attacks thought-out different chapters. The reader may gain a thing or two from the other attacks (i.e. MS08-067 exploitation) but the exploits used in those attacks are something they may not see outside of training environments due to their age.
One Configuration Change for XP VM
One step to perform in addition to what is outlined in the Setting Up Your Virtual Lab chapter is to enable logging for Filezilla (FTP service) on the XP VM. To do so, access FileZill'a admin panel then select Edit -> Settings to get to the configuration window. In the logging section check the Enable Logging selection.
Where to Look
Before diving into the client-side or web application attacks I need to take a moment to outline where the reader needs to look for attack artifacts. I won't go into detail about all of the artifacts and will only cover the pertinent ones to explore the attacks for the Windows VMs.
Windows XP
One of the vulnerable applications installed on Windows XP is XAMPP. XAMPP is an "Apache distribution containing MySQL, PHP and Perl; this provides the VM with vulnerable web services. The following are the logs and artifacts of interest the reader would want to review after the attacks:
Apache logs location: C:\xampp\apache\logs
FileZilla log location: C:\xampp\FileZillaFTP\Logs
The Windows XP operating system artifacts of interest are:
NTFS Master File Table ($MFT)
NTFS Logfile ($Logfile)
Internet explorer browser artifacts
Windows 7
One of the applications installed on the Windows 7 VM is the web service IIS. The book provides a vulnerable web application (called BookApp) that runs on top of IIS. The ISS logging settings can be left in their default configuration. The following are the logs and artifacts of interest the reader would want to review after the attacks:
IIS logs location: C:\inetpub\logs\LogFiles\W3SVC1
Windows HTTP.sys error logging location: C:\Windows\System32\LogFiles\HTTPERR
The Windows 7 operating system artifacts of interest are:
NTFS Master File Table ($MFT)
NTFS Logfile ($Logfile)
NTFS Change Journal ($USNJrnl)
Stay Organized
The last tidbit I'll cover before diving into the attacks is the need to stay organized. As I worked my way through the book I took notes to record when and what attack I performed against what vulnerable VM. This reference made things easier as I was examining the artifacts; it was easier to match up attacks against activity in the artifacts. The screenshot below shows a portion of the notes I kept
Keeping notes is not a necessity but something I highly recommend for beginners.
Client side attacks
Artifacts left by client-side attacks have been well documented on this blog. To name a few: Java was documented here and here, Silverlight discussed here and here while Adobe Reader was mentioned here. Even though some artifacts have already been documented replicating client-side attacks is more beneficial than only reading research done by others. Actually performing the attack against a vulnerable VM shows a completely different perspective and one that can't be attained by just reading about artifacts. The image below shows the Windows XP parsed MFT around the time the system was compromised with the Aurora Internet Explorer exploit (the exploit is the htm page.)
Web Application attacks
The book covers numerous attacks against web applications on the Windows XP, Windows 7, and Ubuntu VMs. The variety of the attacks I thought provided a good starting point for exploring the different ways web servers and applications are compromised. In this post I'm only discussing a few items to demonstrate the traces left in certain artifacts showing these attacks took place.
Vulnerability and Nmap Script Scan Against Windows 7
Chapter 6 walks through a process for finding vulnerabilities on a VM. The chapter has the reader use the following methods: Nessus (vulnerability scanner), Nmap scripting engine (port scanner), Metasploit (exploitation framework), Nikto (web application scanner), and one manual technique. Exploring this aspect for incident response is important since for a system to be compromised a vulnerability had to be exploited. Seeing the traces left by the different methods provides an idea about what one may come across during examinations.
The image below shows the Nessus vulnerability scan activity in the Windows 7 IIS logs. The image is only a small portion of the logs but it illustrates how noisy vulnerability scanners are. This is obvious activity that most monitoring tools will detect fairly quickly. It's also activity that will most likely be tied to people authorized to perform this work for an organization and not an attacker.
In addition to the IIS logs in the W3SVC1 folder, the HTTP.sys error logging provides additional clues about the vulnerability scanning activity as shown below.
The Nmap script scan activity leaves traces in the logs as well but nothing close to the amount left by a vulnerability scanner. The image below shows the Windows 7 IIS logs where the Nmap script scan activity was located (note: the activity will be dependent on the script ran and won't always appear as it does in the image.)
Command Execution Vulnerability Against Windows 7 IIS
Part III in the book has eight different chapters focused on different types of attacks. I won't rehash what all of the attacks are since the book's table of contents is adequate enough. One of the attacks was against a command execution vulnerability, which allows a person to execute commands against the system through the web application. In order to see the command's output - since the web application doesn't display - it requires the attacker (aka reader) to redirect it to a file on the server and then the file is accessed.
The image below shows the command being executed though the "subscribe to a newsletter" functionality (line in the middle.) It's not too apparent what is taking place since the HTTP method used is a POST to send data to the server. The data is not reflected in the URL. However, shortly after the POST there is a GET request for a file on the server named test.txt and the 200 status code means OK (file is there). The POST method may not be too revealing but the GET method reveals a file is on the server.
The server's MFT (parsed into a timeline) provides more clarity about the attack as shown below. The ipconfig.exe program executed at the same time as a new user (georgia) subscribed to a newsletter. Looking at the contents of test.txt shows it contains the ipconfig command output.
PHPAdmin SQL Command Against Windows XP
Another attack that was discussed is leveraging the PHPAdmin panel to execute SQL commands directly against a backend database. The attack involved executing a SQL command that creates a simple web shell on the system; shell only lets you execute commands in a supplied URL.
The Apache logs reveal the attack as seen in the image below. The line for the GET request at 21:17:01 (EDT) shows the URL containing the exact SQL command that creates the file called shell.php. The other highlighted lines show a request for the shell.php file followed by the various commands that were executed through the shell.
The server's MFT parsed into a timeline provides more clarity about the attack as shown below (time is in UTC).
Conclusion
As described in the book's introduction it is for beginners. Those who are new to pen testing field. I also see value in the book for incident response. For those who are either new to incident response without a background in offensive security or those who haven't been exposed to compromised web servers and applications. One shouldn't expect to know everything about investigating systems impacted by client-side and web attacks after working their way through the book. Heck, the reader may never see these exact attacks (outside of pen testers) against production systems. However, the reader will have a better understanding about attack vectors. The means by which an attacker can gain access to a system in order to deliver a payload or malicious outcome. The reader will have an even better understanding about the attack vector artifacts left on those systems. For anyone fitting what I just described should definitely pick up this book, build the VMs, attack the VMs, and then discover what traces they can find. It won't be the last step in their journey but it will be a good first one.
Labels:
attack vectors,
book review,
exploits,
web












Very good read. This is a review with a difference. Thanks..:)